applications of rsa algorithm in cryptography
|
The Application of RSA Encryption Algorithm in the Hainan Rural
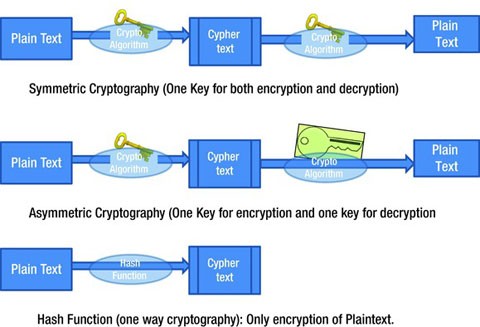
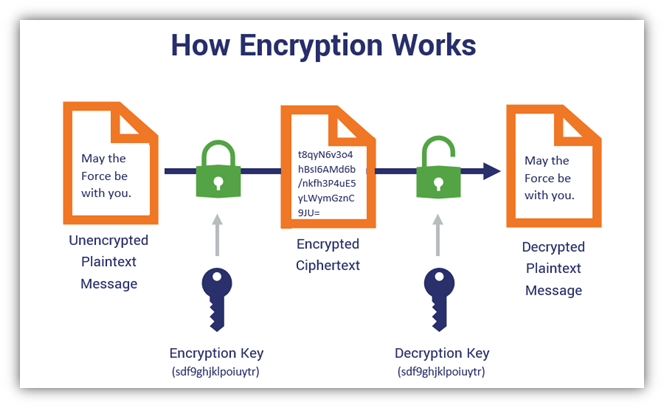
The RSA public-key cryptosystem is an algorithm that converts a plaintext to its corresponding cipher-text and then converts the cipher-text back into its |
What are the applications of RSA in cryptography?
The RSA algorithm is widely used and has been applied in various scenarios, including secure cloud computing environments and wireless networking.
It is the most widely used asymmetric cryptosystem in the world and is used for securing communication in various domains, from cellphone communication to online banking.7 déc. 2023Where is RSA cryptography used?
RSA encryption, type of public-key cryptography widely used for data encryption of e-mail and other digital transactions over the Internet.
It allows the encryption and safe transmission of data without sending decryption keys beforehand.
Digital signatures: RSA algorithm is perfect for digital signatures because the sender can sign a document or message using a private key while the receiver verifies the signature using a public key.
What is the application of public-key cryptography?
The main business applications for public-key cryptography are: Digital signatures - content is digitally signed with an individual's private key and is verified by the individual's public key.
Encryption - content is encrypted using an individual's public key and can only be decrypted with the individual's private key.
- Securing email messages in email providers.
- Encrypting messages in messaging apps and chat rooms.
- Securing P2P data transfer.
- Securing the connection between web browsers and servers.
|
The Application of RSA Encryption Algorithm in the - Atlantis Press
The RSA public-key cryptosystem is an algorithm that converts a plaintext to its corresponding cipher-text, and then converts the cipher-text back into its corresponding plain-text[2] RSA is a public-key cryptography algorithm developed based on the presumed difficulty of cracking the factorial of a large integer[3] |
|
4 Application: RSA cryptography - Andreas Holmstrom
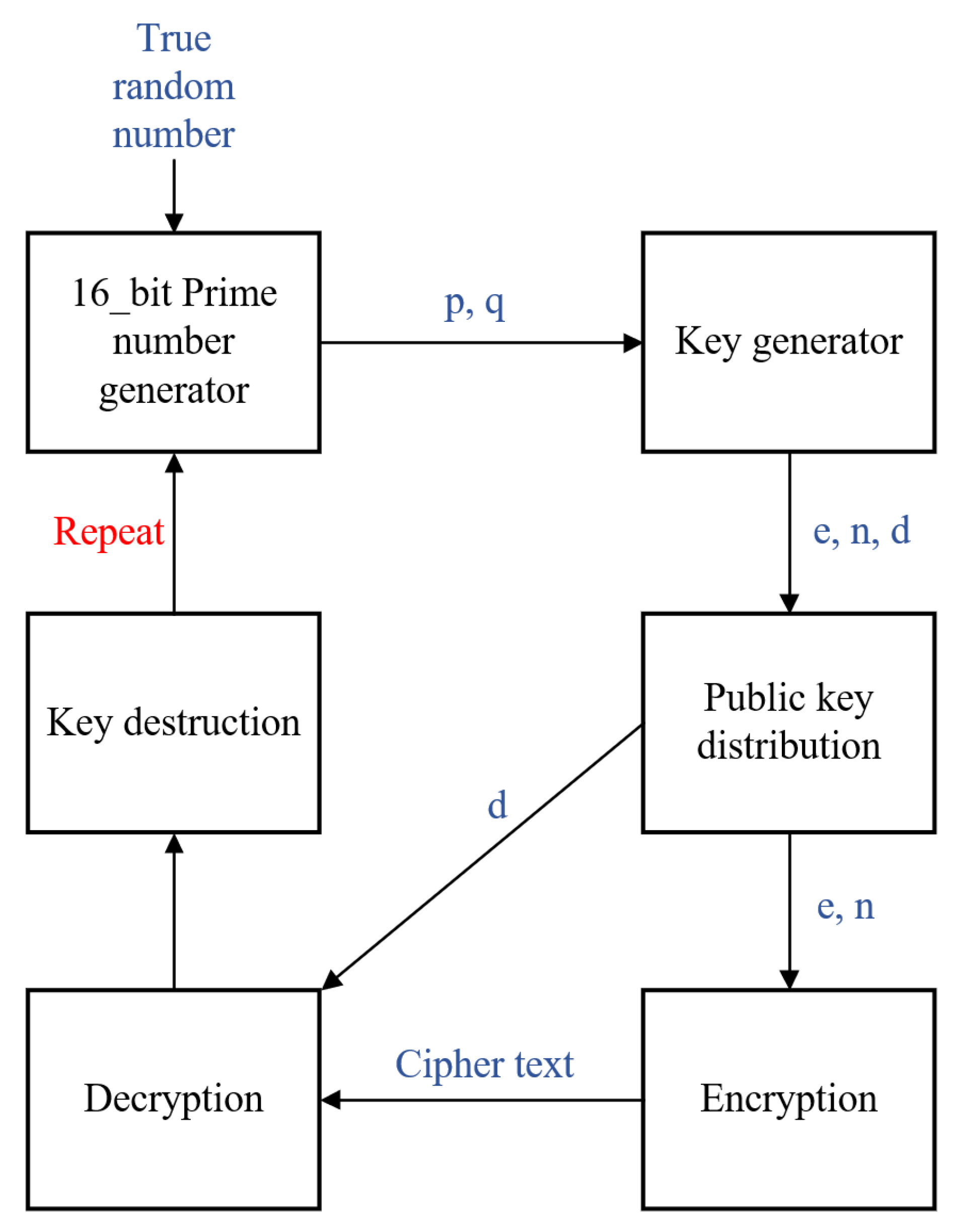
One of the ideas behind the RSA cryptography is that it is very hard to factor large integers small to give an effective encryption for real life applications, but it |
|
Implementation of Rivest Shamir Adleman Algorithm (RSA) and
Adleman (RSA) and Vigenere Cipher cryptographic algorithms to document file either word, excel, and pdf This application includes the process of encryption |
|
Fast and Area Efficient Implementation of RSA Algorithm
Asymmetric cryptosystem has two different keys for the encryption and decryption algorithm [10, 11] These two keys have to be generated or shared between the |
|
High Speed Implementation of RSA Algorithm with Modified Keys
RSA Cryptosystem, Asymmetric encryption is relatively slow and therefore unsuitable for encryption of large messages [11] [9][4] [10] The RSA public-key |
|
The RSA Algorithm
3 jui 2009 · Everyone has their own encryption and decryption keys The keys The security of the RSA algorithm has so far been validated, since no known attempts This has obvious implications of importance in real-life applications |
|
METHODS TOWARD ENHANCING RSA ALGORITHM - SSRN Papers
Cryptography uses a key, or some sort of a password to either encrypt or Cryptography, RSA Algorithm, Encryption, Decryption, Cryptosystem, Security, Public |


















![PDF]J Katz _ Y Lindell Introduction to Modern Cryptographypdf PDF]J Katz _ Y Lindell Introduction to Modern Cryptographypdf](https://0.academia-photos.com/attachment_thumbnails/52433450/mini_magick20190122-20887-11060cy.png?1548227033)


![PDF] Cryptographic Algorithms : Applications in Network Security PDF] Cryptographic Algorithms : Applications in Network Security](https://demo.fdocuments.in/img/742x1000/reader019/reader/2020033121/5ab868957f8b9ad13d8c8312/r-1.jpg?t\u003d1610378897)