heap chunk structure
|
Understanding the heap by breaking it
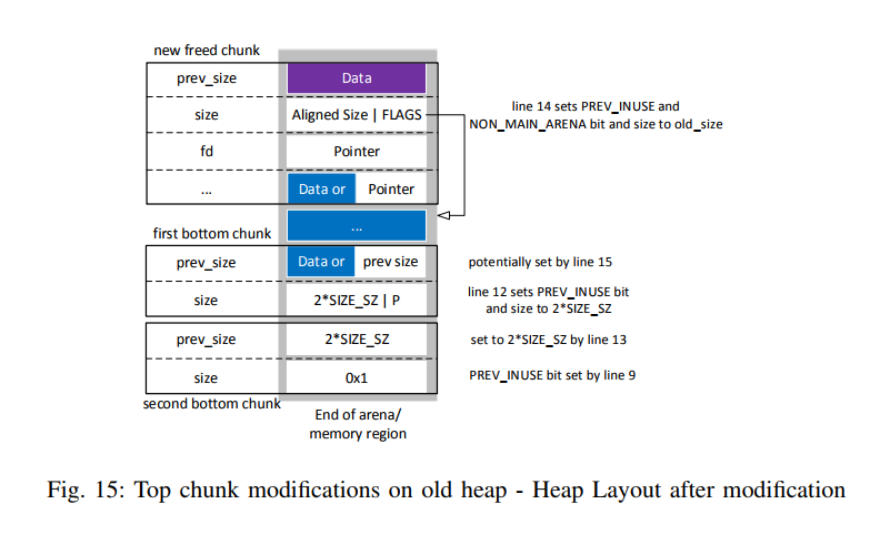
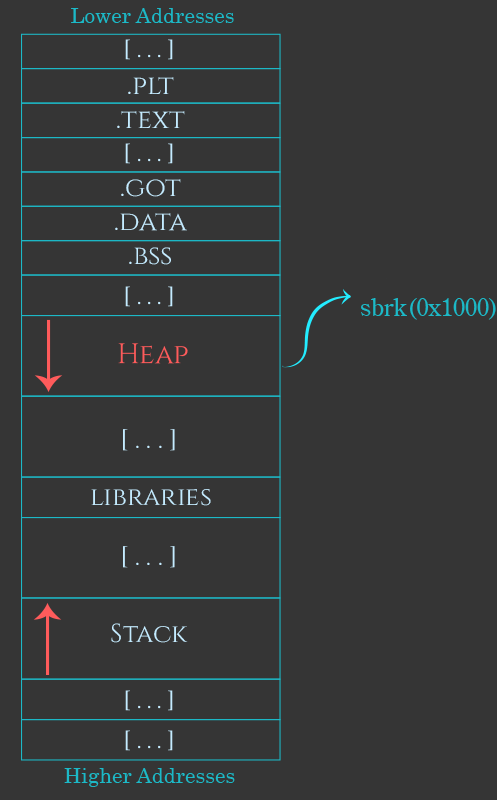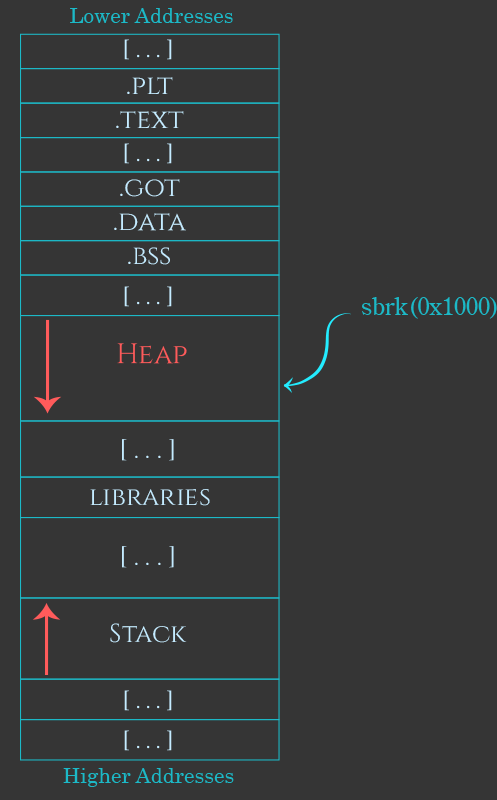
allocated from this top chunk but as memory use progresses chunks are usually of the heap and provides a pointer to the arena data structure. |
|
A Malloc Tutorial
16 févr. 2009 2 The Heap and the brk and sbrk syscalls ... 5.2 Finding a chunk: the First Fit Algorithm . ... Figure 3: Heap's Chunks Structures. |
|
Heap Overflows Illustrated 1.0
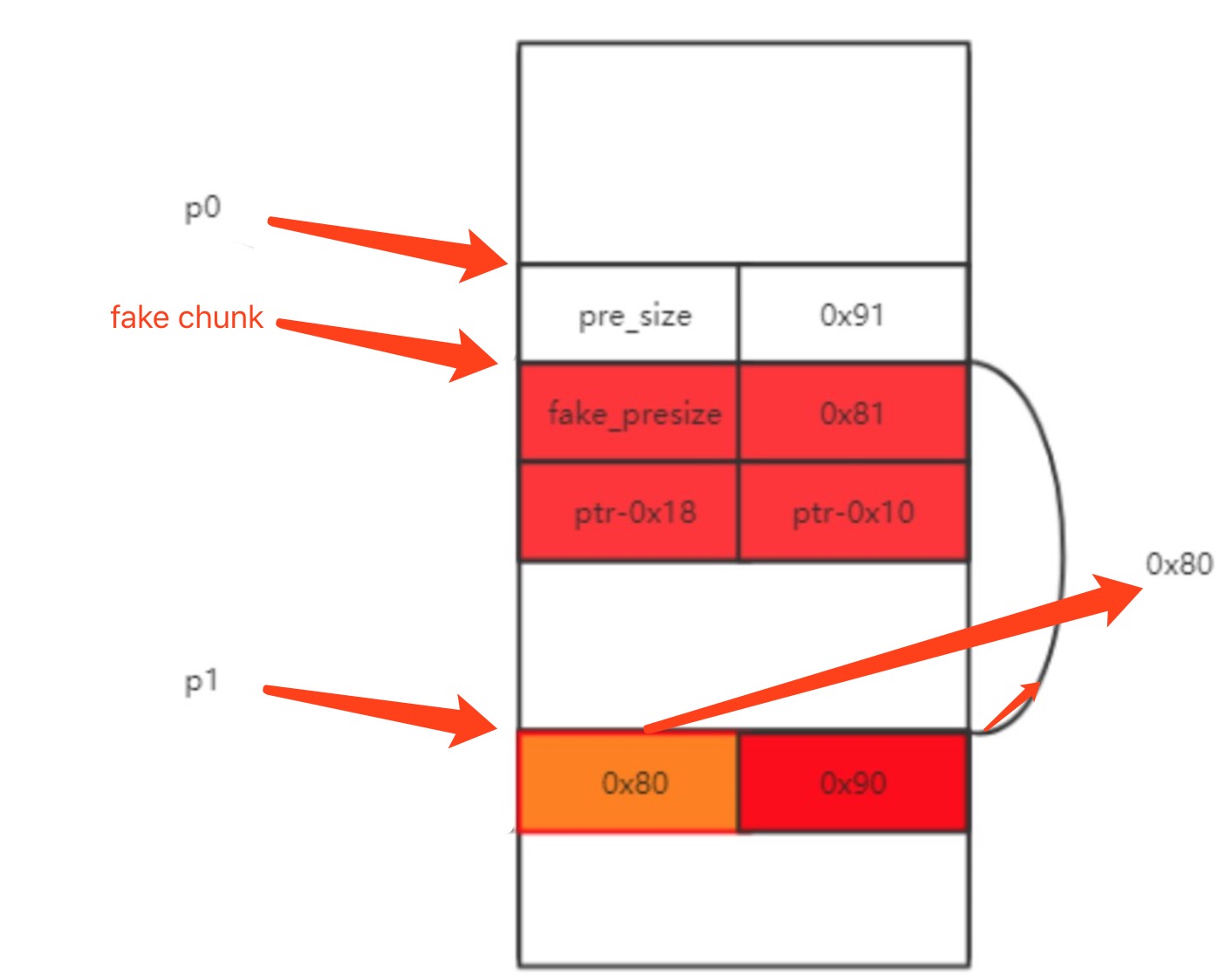
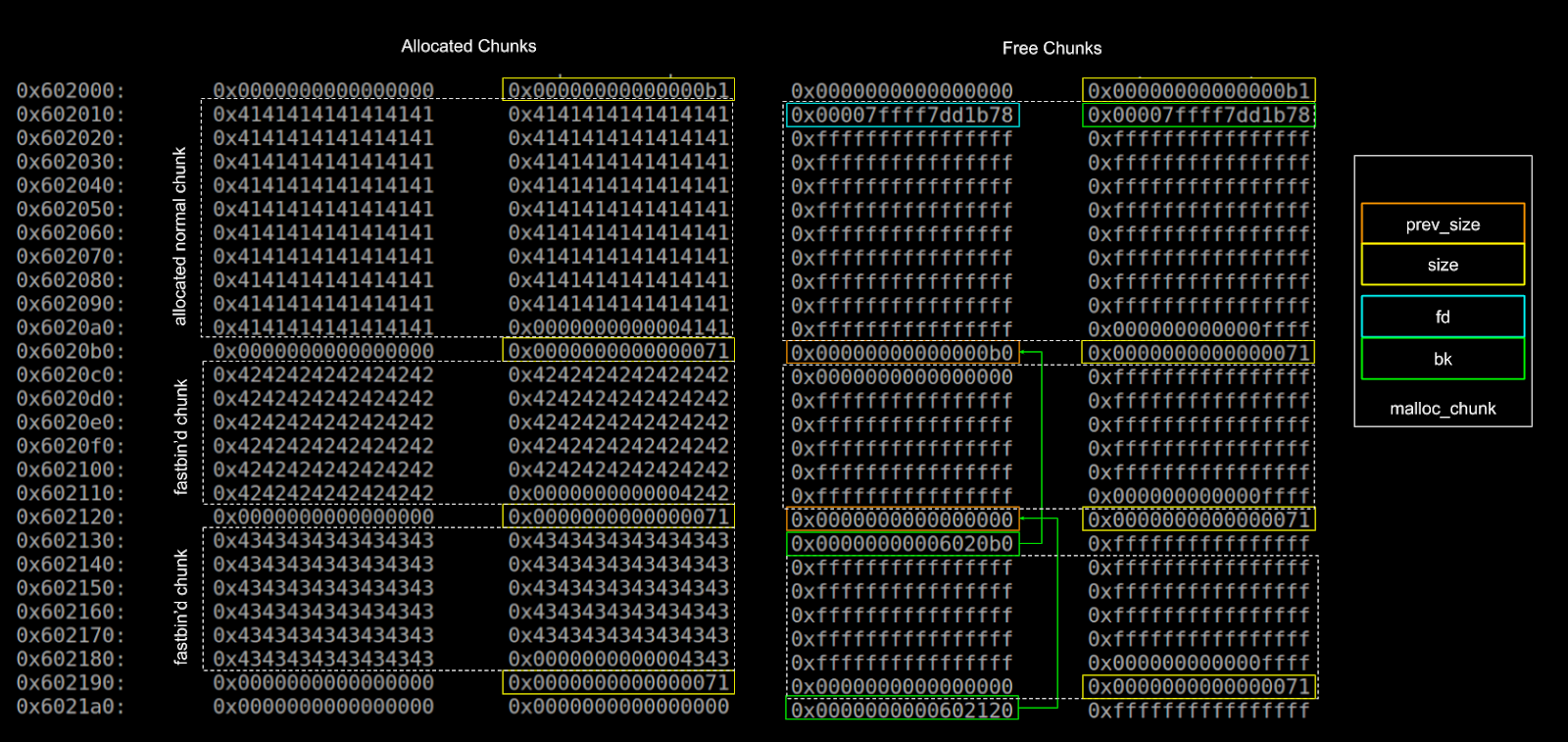
“M” flags overflowing the heap chunk into the next allocated chunk. This attack uses hundreds of fake heap structures to force unlink to copy the ... |
|
Unlink Attack Defense Method Based on New Chunk Structure
19 juil. 2019 The Unlink attack is a way of attacking the heap overflow vulnerability under the Linux platform. However because the heap overflow data ... |
|
Understanding the Low Fragmentation Heap
UserBlocks – A _HEAP_USERDATA_HEADER structure coupled with this SubSegment which holds a large chunk of memory split into n-number of chunks. AggregateExchg – |
|
Understanding the Low Fragmentation Heap
A chunk is a contiguous piece of memory that can be measured in either blocks or bytes. HeapBase is a pseudonym for a pointer to a _HEAP structure as |
|
Attacking the Vista Heap
“termination on heap corruption” option. – Overwrite low fragmentation heap's bucket structure. – Partial overwrite of LFH heap chunk |
|
WINDOWS 10SEGMENT HEAP INTERNALS
Introduced in Windows 10 Segment Heap is the native heap implementation used in In this presentation |
|
One Size Fits All Unravelling PCI
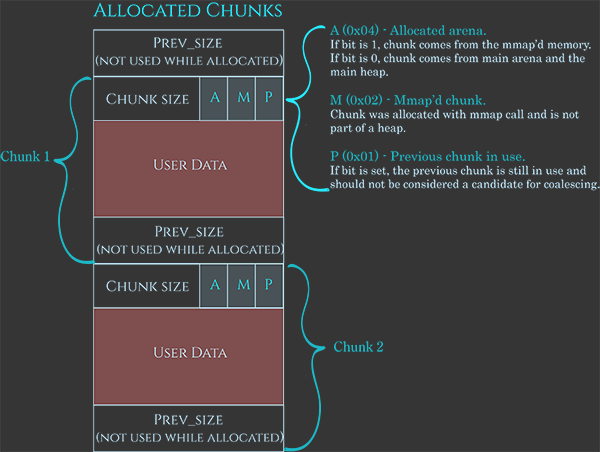
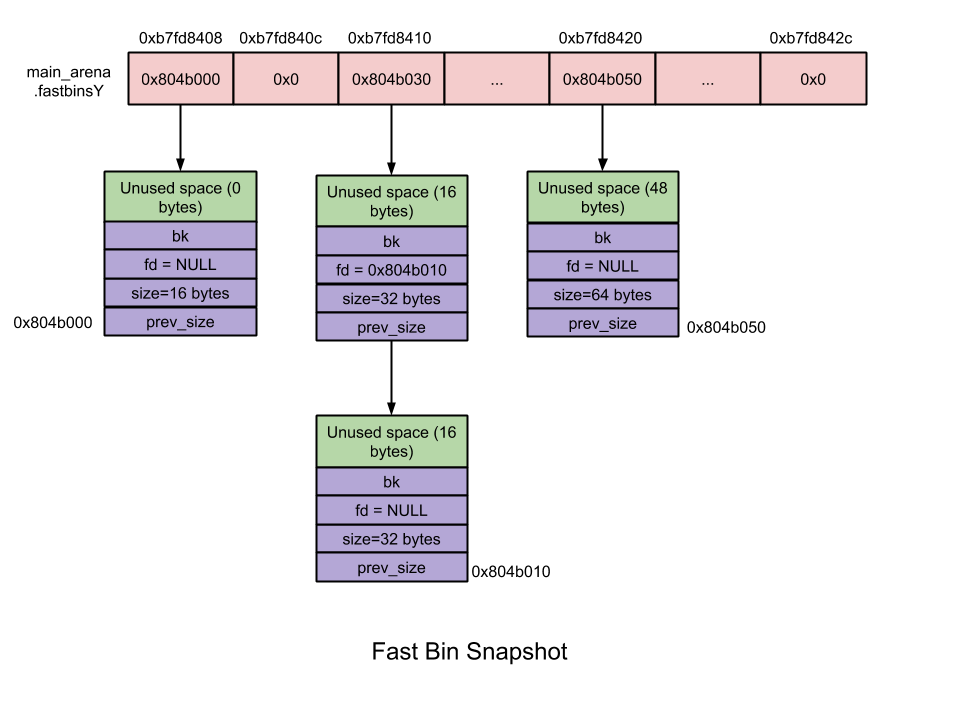
if free pointer to the previous malloc_chunk. ? most commonly known heap data structure. ? Interpretation of chunk changes varying on state. (important!) |
|
Glibc Adventures - The Forgotten Chunks
28 janv. 2015 3 Abusing Heap Structures. 5. 3.1 Glibc's Heap Structure Overview. 5. 3.2 Producing Overlapping Chunks. 6. 3.2.1 Extending Free Chunks. |
|
Understanding the heap by breaking it - Black Hat
The structure above provides an accurate depiction of a given chunk of memory regardless of its state (only what members are used differs) Even more this |
|
Understanding the heap by breaking it - Black Hat
A case study of the heap as a persistent data structure Allocation requests are filled from either the 'top' chunk or free lists |
|
Heap Management
The heap is the portion of the store that is used for data that lives indefinitely or until the program explicitly deletes it |
|
Heap Overflows Illustrated 10 - CiteSeerX
Chunks are areas of memory in the heap that are dynamically allocated via commands such as malloc (memory allocation) and are later returned to the available |
|
Heap exploitation
23 nov 2020 · The pointer to the header is instead called the chunk pointer and can be obtained from the user pointer by subtracting the header size (8 bytes |
|
Dynamic Memory Allocation in the Heap
Keep track of free blocks 3 Pick a block to allocate 4 Choose what do with extra space when allocating a structure that is smaller than |
|
Heap-exploitationpdf - The Swiss Bay
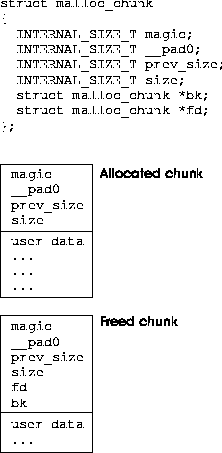
27 mar 2017 · This structure represents a particular chunk of memory The various fields have different meaning for allocated and unallocated chunks struct |
|
Windows 8 Heap Internals - Illmaticscom
http://illmatics com/Understanding_the_LFH_Slides pdf structure in RtlpFreeHeap() Hope to encapsulate virtual chunk in inaccessible memory |
|
History and Current State of Heap Exploit
_HEAP structure resides at the beginning of a heap and the address is To manage free chunks Windows heap manager uses doubly cyclic linked list |
|
CS-UY 3943-G / CS-GY 9223-H
Looked at the data structures of the glibc allocator Different bins may use different data structures or allocation strategies Heap Chunk Structure |
|
Understanding the heap by breaking it - Black Hat
The heap is a global data structure that provides dynamically allocated memory storage that provides an 'exists until free' scope It provides a compliment to the stack in that it allows an application to allocate space for variables at run time that can exist outside the scope of the currently executing function |
|
Heap Overflows Illustrated 10
“M” flags, overflowing the heap chunk into the next allocated chunk This attack uses hundreds of fake heap structures to force unlink to copy the contents of bk |
|
Heap Exploitation - Lao-Yuans Blog
This structure represents a particular chunk of memory The various fields have different meaning for allocated and unallocated chunks struct malloc_chunk { |
|
Comprehensively and Efficiently Protecting the Heap ∗
Heap chunk structure used in GNU C [11] 1 Actually, since heap chunks are 8- byte aligned, the last three bits in the size numeric field are used to store the PIU |
|
Understanding the Low Fragmentation Heap - Illmaticscom
A chunk is a contiguous piece of memory that can be measured in either, blocks or bytes HeapBase is a pseudonym for a pointer to a _HEAP structure as defined |
|
Linux Heap Internalskey - GitHub
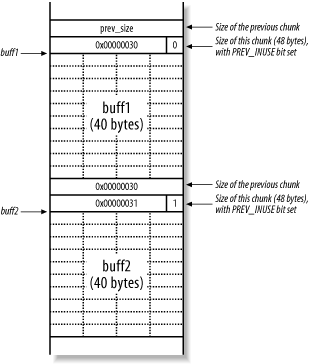
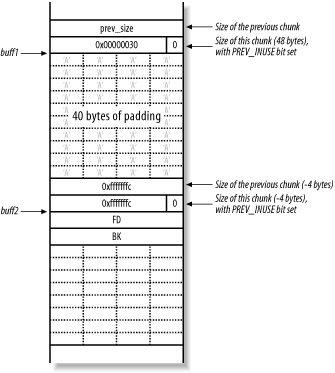
INTRODUCTION PREV_SIZE SIZE FD BK USER DATA PREV_SIZE SIZE Chunk Next Chunk Mem GLIBC Heap Structure Logical description In memory |
|
Investigation of x64 glibc heap exploitation techniques - UiO - DUO
A chunk can either be in use or free Every running program as a "arena", this is a special data structure which contains a pointer to one more more heaps Heap |
|
Attacking the Vista Heap - Inertia War
Overflow Summary • A heap overflow can potentially overwrite: – Internal heap structures • Chunk headers • Bucket structures • Main heap structure |