nist 800 53 awareness and training
|
NIST SP 800-50 Building an Information Technology Security
The two publications are complementary – SP 800-50 works at a higher strategic level discussing how to build an IT security awareness and training program |
|
FISMA and OPM Awareness and Training Requirements and
OPM awareness and training requirements. • NIST SP 800-50 highlights. • NIST SP 800-16 highlights. • Possible changes to SP 800-16. • NIST SP 800-53 |
|
Security and Privacy Controls for Information Systems and
Sep 5 2020 HISTORICAL CONTRIBUTIONS TO NIST SPECIAL PUBLICATION 800-53 ... the associated awareness and training controls;. |
|
FISMA & OPM Awareness 7 Training Requirements & Related NIST
NIST SP 800-16 and Rev. 1. • NIST SP 800-53 Allowable cost: “Costs of training and education that are ... Develop awareness and training plan. |
|
Protecting Controlled Unclassified Information in Nonfederal
Feb 22 2021 Mapping NIST Special Publication 800-53 security controls to the ... Provide security awareness training on recognizing and reporting ... |
|
Security and Privacy Controls for Federal Information Systems and
Sep 23 2021 baseline security controls in NIST Special Publication 800-53 |
|
NIST SP 800-66 Revision 1 An Introductory Resource Guide for
Security Awareness and Training (§ 164.308(a)(5)) . detailed in NIST SP 800-53 Recommended Security Controls for Federal Information. Systems. |
|
(3rd Draft) NIST SP 800-16 Rev. 1 A Role-Based Model for Federal
Mar 14 2014 Security Awareness and Training Program” identifies aspects of an effective ... NIST SP 800-53 |
|
ITL Bulletin How To Identify Personnel With Significant
Security Awareness and Training Program (October 2003). (August 2009) and SP 800-53A |
|
FISSEA Conference Presentation
Jul 20 2020 Building a Security Awareness and Training Program (NIST SP 800-50). • Federal Information Security Educators (FISSEA). Training. |
|
Security and Privacy Controls for Information Systems - NIST
National Institute of Standards and Technology Special Publication 800 -53 Revision 5 Natl Inst Stand Technol Spec Publ 800-53 Rev 5 492 pages (September 2020) CODEN: NSPUE2 This publication is available free of charge from: https://doi org/10 6028/NIST SP 800-53r5 Comments on this publication may be submitted to: |
|
Security and Privacy Controls for Information - NIST Page
Mar 28 2018 · NIST Special Publication 800- 53A • Supports RMF Step 4 (Assess) • Is a companion document to 800-53 • Is updated shortly after 800-53 is updated • Describes high level procedures for assessing security controls for effectiveness • Defines assessment procedures using – Assessment Objectives – Assessment Methods – Assessment Objects |
|
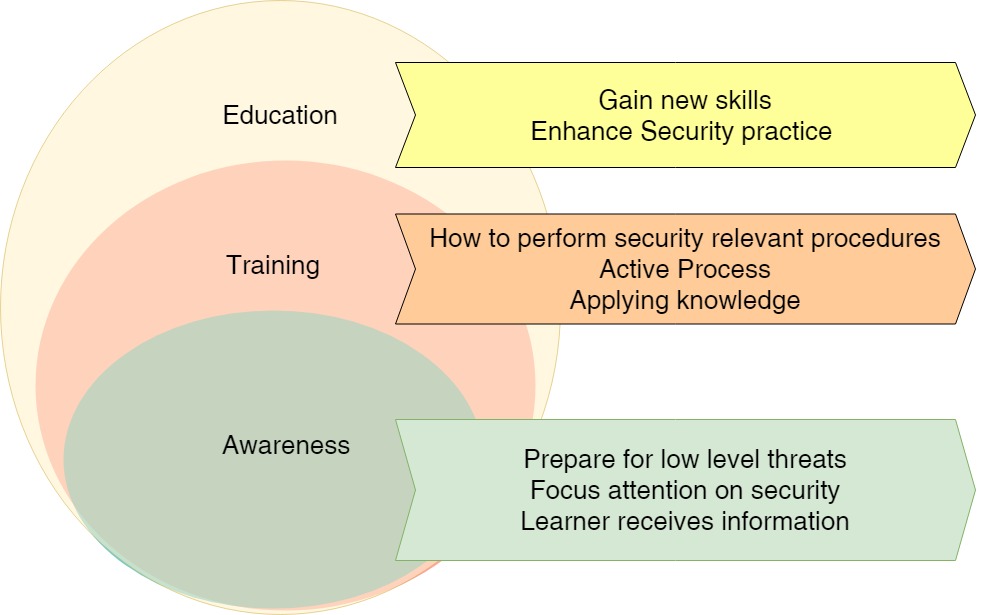
IT System Awareness and Training (AT) Standard
awareness and training procedures annually (i e each fiscal year) and following the identification of evolving threats issuance of new or significantly changed existing Federal laws executive orders directives regulations and ED policies identification of emerging technology |
|
FISMA and OPM Awareness and Training Requirements and Related
NIST SP 800-50 Says • Conduct needs assessment • Develop awareness and training plan • Entire workforce should be exposed to awareness material annually • A continuous awareness program using various methods of delivery throughout the year can be very effective • Identify employees with significant |
|
Le d-ib td-hu va-top mxw-100p>KnowBe4® - Official Site - Security Awareness Training
Jan 31 2022 · (NIST) Special Publication (SP) 800-53 Security and Privacy Controls for Information Systems and Organizations 4 as baseline information system controls This governance document establishes Department information technology (IT) system awareness and training standards necessary to improve the efficiency of operation or security of |
|
NIST SP 800-50 Building an Information Technology Security
NIST Special Publication 800-50 Building An Information Technology Security Awareness and Training Program provides guidance for building an effective |
|
NISTSP800-53r5pdf
5 sept 2020 · NIST is responsible for developing information security standards and guidelines including minimum requirements for federal information systems |
|
SP 800-50 Building an Information Technology Security Awareness
1 oct 2003 · NIST Special Publication 800-50 Building An Information Technology Security Awareness and Training Program provides guidance for building |
|
Awareness Training & Education CSRC
Publications related to the project Awareness Training Education SP 800-181 National Initiative for Cybersecurity Education (NICE) Cybersecurity |
|
Security and Privacy Controls for Federal Information Systems and
23 sept 2021 · baseline security controls in NIST Special Publication 800-53 information systems (e g security awareness training incident response |
|
FISMA and OPM Awareness and Training Requirements and
OPM awareness and training requirements • NIST SP 800-50 highlights • NIST SP 800-16 highlights • Possible changes to SP 800-16 • NIST SP 800-53 |
|
Recommended Security Controls for Federal Information Systems
NIST Special Publication 800-53 Revision 1 167 pages Security awareness training to inform personnel (including contractors and other users of |
|
Building a Cybersecurity and Privacy Awareness and Training
21 sept 2021 · Cybersecurity awareness and training resources methodologies and requirements have evolved since NIST Special Publication (SP) 800-50 |
|
SP 800-50 Rev 1 (Draft) Building a Cyber and Privacy Awareness
21 sept 2021 · The new proposed title for SP 800-50 is Building a Cybersecurity and Privacy Awareness and Training Program The public is invited to provide |
|
110 – Security Awareness and Training Standard WI DET
8 juil 2022 · This standard uses the NIST SP 800-53 Rev 5 framework as the guideline to establish control objectives to address a diverse set of security |
Do information security standards and guidelines apply to national security systems?
- Such information security standards and guidelines shall not apply to national security systems without the express approval of the appropriate federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130.
How can organizations use vulnerability analysis to support penetration testing?
- Organizations can use the results of vulnerability analyses to support penetration testing activities. Penetration testing can be conducted internally or externally on the hardware, software, or firmware components of a system and can exercise both physical and technical controls.
How do organizations conduct a contingency test?
- Organizations conduct testing based on the requirements in contingency plans and include a determination of the effects on organizational operations, assets, and individuals due to contingency operations. Organizations have flexibility and discretion in the breadth, depth, and timelines of corrective actions. Related Controls:
What are 31 trustworthiness requirements?
- 31 Trustworthiness requirements can include attributes of reliability, dependability, performance, resilience, safety, security, privacy, and survivab ility under a range of potential adversity in the form of disruptions, hazards, threats, and privacy risks.
|
I N F O R M A T I O N S E C U R I T Y - NIST Technical Series
Security awareness training to inform personnel (including contractors and The catalog of security controls provided in Special Publication 800-53 can be |
|
FISMA and OPM Awareness and Training Requirements and
OPM awareness and training requirements • NIST SP 800-50 highlights • NIST SP 800-16 highlights • Possible changes to SP 800-16 • NIST SP 800-53 |
|
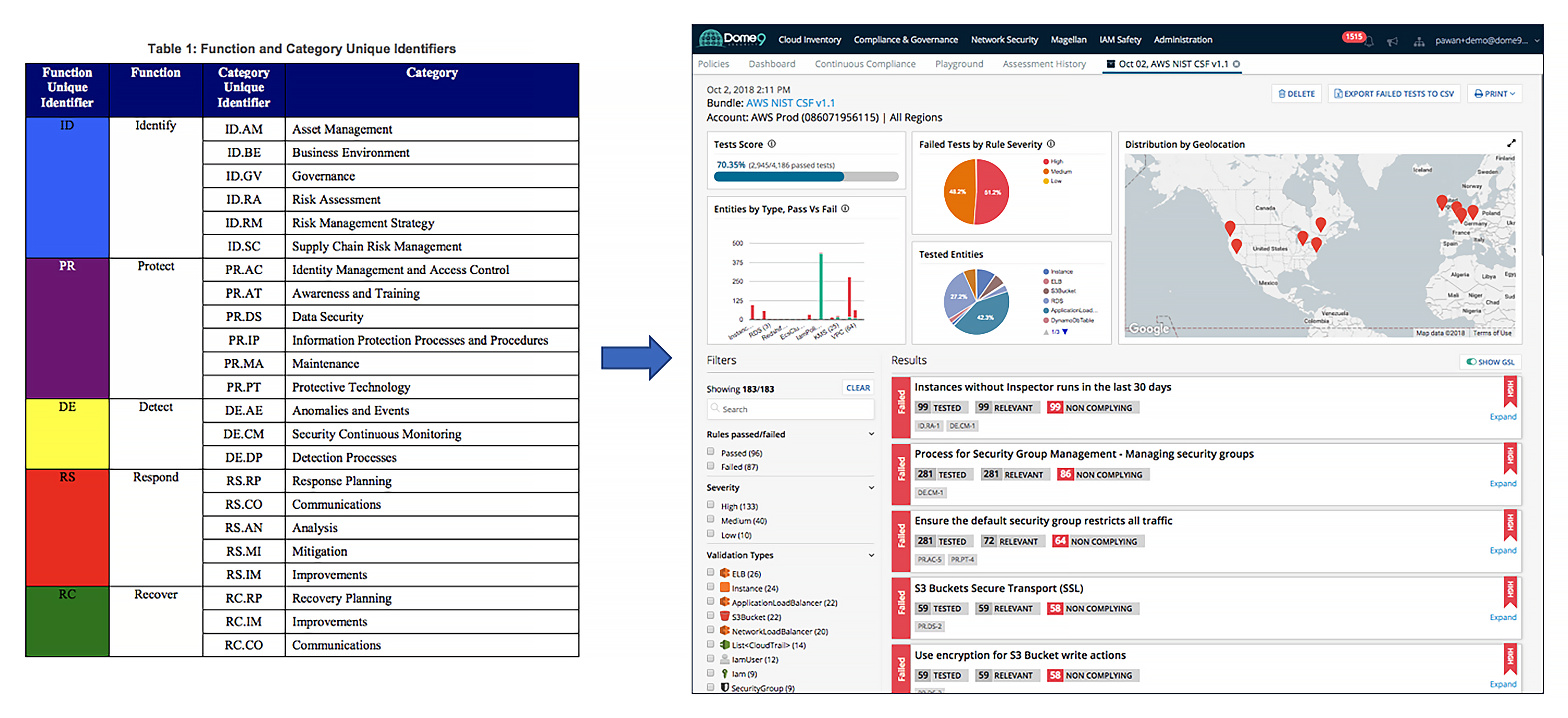
NIST SP 800-53 - NIST Technical Series Publications
15 jan 2014 · baseline security controls in NIST Special Publication 800-53, Security organizational information systems (e g , security awareness training, |
|
FISSEA 2006 - FISMA & OPM Awareness 7 Training Requirements
and Rev 1 • NIST SP 800-53 Allowable cost: “Costs of training and education that are related to the Develop awareness and training plan • All users of |
|
Example NIST 800-53 rev4 Low Moderate Policies - Examples
PL-5: PRIVACY IMPACT ASSESSMENT [WITHDRAWN FROM NIST 800-53 REV4] 32 AT-2(2): Security Awareness Training Insider Threat 52 |
|
Information Security – Awareness and Training Procedures - US EPA
16 fév 2016 · All EPA information systems must meet the security requirements through the use of the security controls defined in the NIST SP 800-53, |
|
Security Awareness and Training Policy - Document Approval
29 jan 2018 · and monitoring of the security awareness training program the Security Awareness and Training principles established in NIST SP 800-53, |
|
Unemployment Insurance - ETA Advisories
2 nov 2020 · accordance with the guidance provided in NIST SP 800-53 to protect PII: • Access Security awareness training to inform personnel (including |
|
SP 800-53A - FISMA Center
71 National Institute of Standards and Technology Special Publication 800-50, Building an Information Technology Security Awareness and Training Program, |
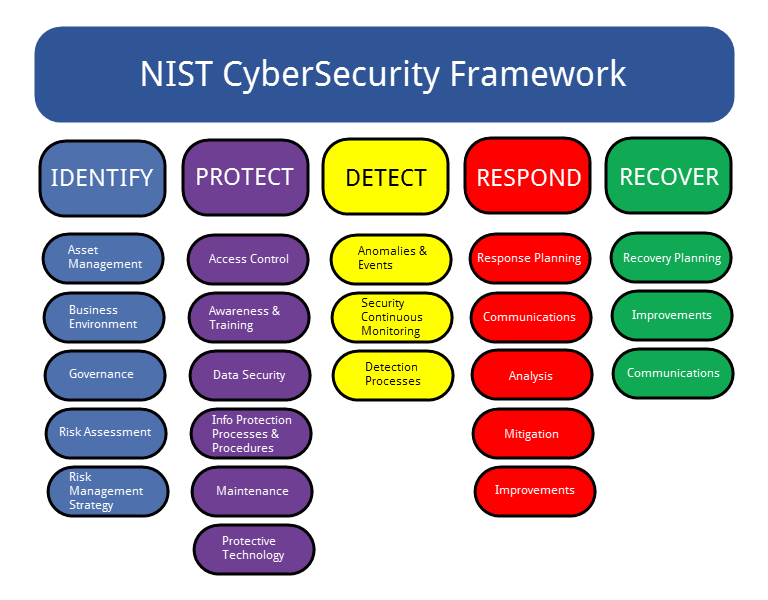
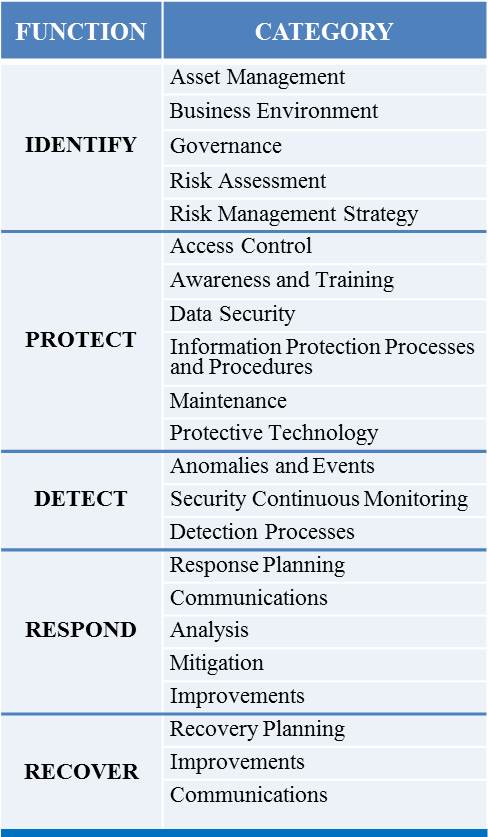
![NIST - Cybersecurity Framework mindmap - [PDF Document] NIST - Cybersecurity Framework mindmap - [PDF Document]](https://www.givainc.com/images/NIST-Cyber-Framework.png)



















![PDF] An Introduction to Computer Security free tutorial for Beginners PDF] An Introduction to Computer Security free tutorial for Beginners](https://www.cci.msstate.edu/nist-training/img/startslide.png)

