plan design and implement information security
|
How to Implement Security Controls for an Information Security
series Information Security Management System Planning for CBRN Facilities2 Similarly |
|
Implementation Methodology for Information Security Management
For example the supply chain management system or enterprise resource planning system or client relationship management process of the organization. The IT |
|
01/12/2017 CHIEF INFORMATION SECURITY OFFICER 1404
12 janv. 2017 (CISO) manages the design development |
|
Information Security Plan
Design and Implementation of Safeguards Program . This Information Security Plan describes Western Kentucky University's safeguards to protect data. |
|
Security of nuclear information
It is essential that all nuclear and other radioactive overall planning design and implementation of security measures. Furthermore |
|
A Success Strategy for Information Security Planning and
Citadel Information Group designs and implements information security management programs to meet client needs for effective information security risk |
|
Principles of Information Security Fourth Edition
Organization translates blueprint for information security into a concrete project plan implementation of information security project plan. |
|
CPG 234 Information Security
The life-cycle phases consist of: planning design |
|
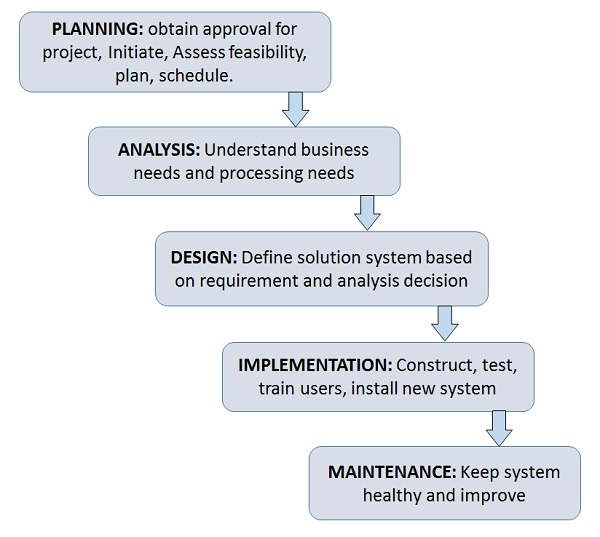
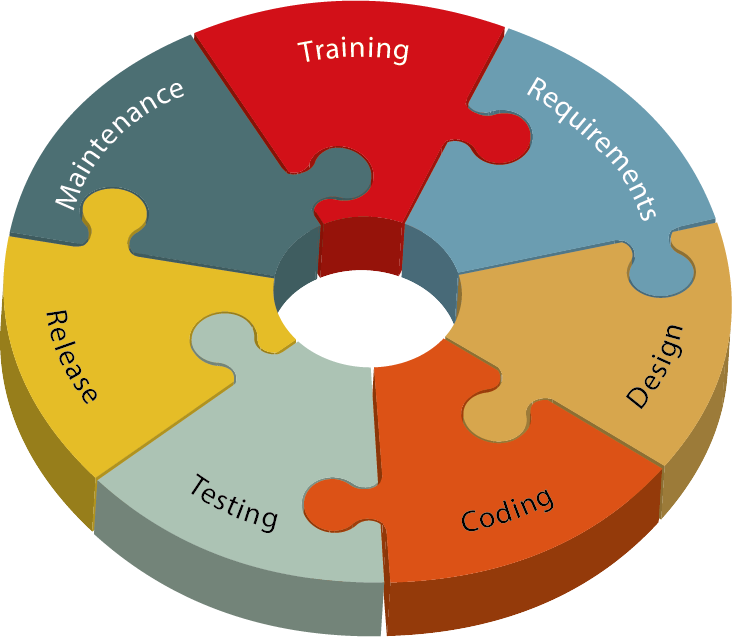
THE SYSTEM DEVELOPMENT LIFE CYCLE (SDLC)
design implementation and maintenance to disposal There are many different SDLC models and methodologies but each generally consists of a series of defined steps or phases For any SDLC model that is used information security must be integrated into the SDLC to ensure appropriate protection for the information that the system will |
|
Guide for developing security plans for federal
Guide for Developing Security Plans for Federal Information Systems Authority This document has been developed by the National Institute of Standards and Technology (NIST) in furtherance of its statutory responsibilities under the Federal Information Security Management Act of 2002 Public Law 107-347 |
|
CCISO - EC-Council
• Develop a plan for information security encryption techniques 2 Vulnerability Assessment and Penetration Testing • Design develop and implement a penetration testing program based on penetration testing methodology to ensure organizational security • Identify different vulnerabilities associated with information systems and legal issues |
|
How to Implement Security Controls for an Information - PNNL
In this document the reader will be introduced to risk-based security controls that are associated with each of the information security plans or planning components that are used to develop and implement an ISMS These include three risk management components and eight other security components |
|
Creating a Written Information Security Plan for your Tax
Creating a Written Information Security Plan (WISP) for your Tax & Accounting Practice 2 Requirements 2 Getting Started on your WISP 3 WISP - Outline 4 Sample Template 5 Written Information Security Plan (WISP) 5 Added Detail for Consideration When Creating your WISP 13 |
|
Le d-ib td-hu va-top mxw-100p>KnowBe4® Security Training - Security Awareness Training
This System Security Plan provides an overview of the security requirements for the system name< > and describes the controls in place or planned for implementation to provide a level of security appropriate for the information to be transmitted processed or stored by the system |
What is a system security plan?
- See System Security Plan. Requirements levied on an information system that are derived from laws, executive orders, directives, policies, instructions, regulations, or organizational (mission) needs to ensure the confidentiality, integrity, and availability of the information being processed, stored, or transmitted.
What are the key elements of a security plan?
- Another essential element is the development of security plans, which establish the security requirements for the information system, describe security controls that have been selected, and present the rationale for security categorization, how controls are implemented, and how use of systems can be restricted in high-risk situations.
What should a facility do when developing an information security program?
- When developing an information security program or an ISMS, the facility should identify their information systems and assets, determine the risks associated with these systems and assets, and evaluate methods for controlling or reducing these risks.
How do you protect information and Information Systems?
- The most effective way to protect information and information systems is to integrate security into every step of the system development process, from the initiation of a project to develop a system to its disposition.
|
How to Implement Security Controls for an Information - PNNL
facilities need to design, implement, and maintain an information security It describes a risk-based approach for planning information security programs based |
|
Success Strategy for Infosec Planning and Implementation - Citadel
THE INFORMATION SECURITY PLANNING CHALLENGE 3 PREPARING TO implementation life-cycle, similar to the following System Modeling Design |
|
Implementation of information security policies in public - DiVA
implementation of an information security in organizations, with a specific focus on Design phase: This phase should include a plan for how policies should be |
|
Advice 35 Implementing Information Security Part 1 - Office of the
Part 2: A Step by Step approach to developing an Information Security Plan Responsibility for implementing Information security needs to be assigned to staff at an security policy and goes on to present a design for a suite of information |
|
How to design and implement a cyber security strategy - Tait
Network segmentation plan (firewalls, secure architecture, locking down unused ports, deploy- ing 'data diodes' where one-way communications is sufficient) • |
|
IT Security Plan - University of South Florida
Vulnerability A flaw or weakness in a USF information system security procedures, design, implementation, or internal controls that could be accidentally or |




![PDF] Information Security: Design Implementation Measurement and PDF] Information Security: Design Implementation Measurement and](https://www.protectivesecurity.gov.au/sites/default/files/2019-09/govsec03-annexa-fig1_lrg.png)



![PDF] Information Security: Design Implementation Measurement and PDF] Information Security: Design Implementation Measurement and](https://www.protectivesecurity.gov.au/sites/default/files/2019-09/govsec03-annexa-fig3_lrg.png)