apple itunes law enforcement contact
|
Legal Process Guidelines
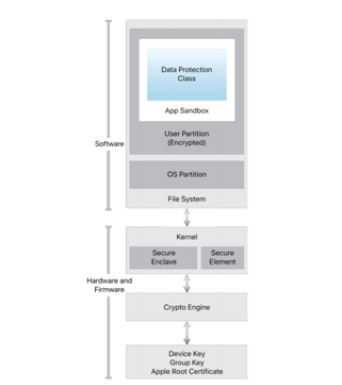
Apple has a centralized process for receiving tracking processing and responding to legitimate legal requests from government law enforcement and private parties from when they are received until when a response is provided |
| EMERGENCY Government / Law Enforcement Information Request |
|
Legal Process Guidelines – Apple
If you choose to send an email to this address it must be from a valid and official government or law enforcement email address. Subpoenas |
|
Legal Process Guidelines - Apple
If you have further questions please contact lawenforcement@apple.com. Apple Store Gift Cards and App Store & iTunes Gift Cards have a serial number. |
|
Outside US Guidelines June 2017 (3) 2017.06.23
23-Jun-2017 Online Store and iTunes related personal information may also be ... For government and law enforcement information requests Apple complies ... |
|
Law-enforcement-guidelines-emeia.pdf
08-Jun-2017 Online Store and iTunes related personal information may also be ... an official government or law enforcement email address to the mailbox:. |
|
Government / Law Enforcement Information Request - Apple Legal
Apple's Legal Process Guidelines for Government &Law Enforcement outside the United States Official Government or Law Enforcement Email Address: Phone:. |
|
V13a US LE Guidelines 10.6.14.pages
17-Sept-2014 and applications through the iTunes Store App Store |
|
V13a US LE Guidelines 10.6.14.pages
17-Sept-2014 and applications through the iTunes Store App Store |
|
Apple Privacy
the iTunes Store App Store |
|
Legal-process-guidelines-apac.pdf
applications through the iTunes Store App Store |
|
Legal-process-guidelines-emeia.pdf
applications through the iTunes Store App Store |
|
Government / Law Enforcement Information Request - Apple
Agency Name: Requesting Officer Name Title/Rank: Official Government or Law Enforcement Email Address: Phone: Case Context Case Date Location: |
|
Legal Process Guidelines - Apple
Apple accepts service of legally valid government or law enforcement information requests by email from government and law enforcement agencies, provided |
|
Outside US Guidelines June 2017 (3) 20170623 - Apple
23 jui 2017 · Online Store and iTunes related personal information may also be an official government or law enforcement email address to the mailbox: |
|
Guide to Obtaining Communication Service Provider - IRIS LLC
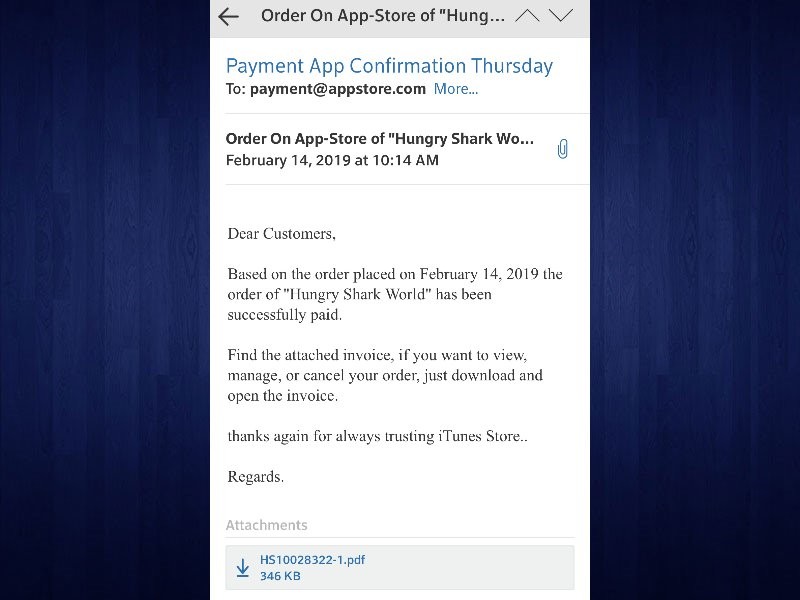
obtained by contacting a number of sources, including U S law enforcement attachés located When iTunes gift cards are activated, Apple records the name of |
|
Do you know what iTunes vouchers are ? - West Yorkshire Police
As the fraudsters are sometimes using iTunes Gift Cards, Apple want to make the card will likely be spent before you are able to contact Apple and law |
|
EuroMed Police Digital Evidence Manual - EJN - europaeu
to better address the judicial and law enforcement requests, with particular support When iTunes gift cards are activated, Apple records the name of the store, |
|
Forensic investigation of iPhone - DiVA
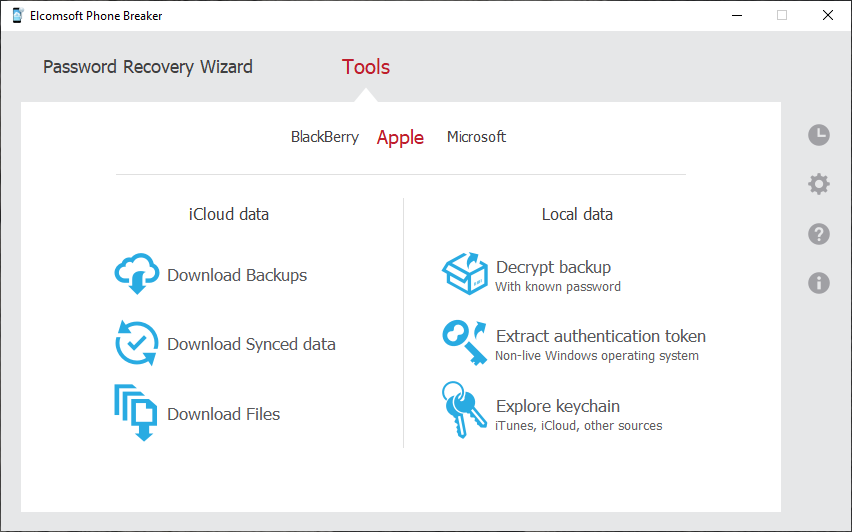
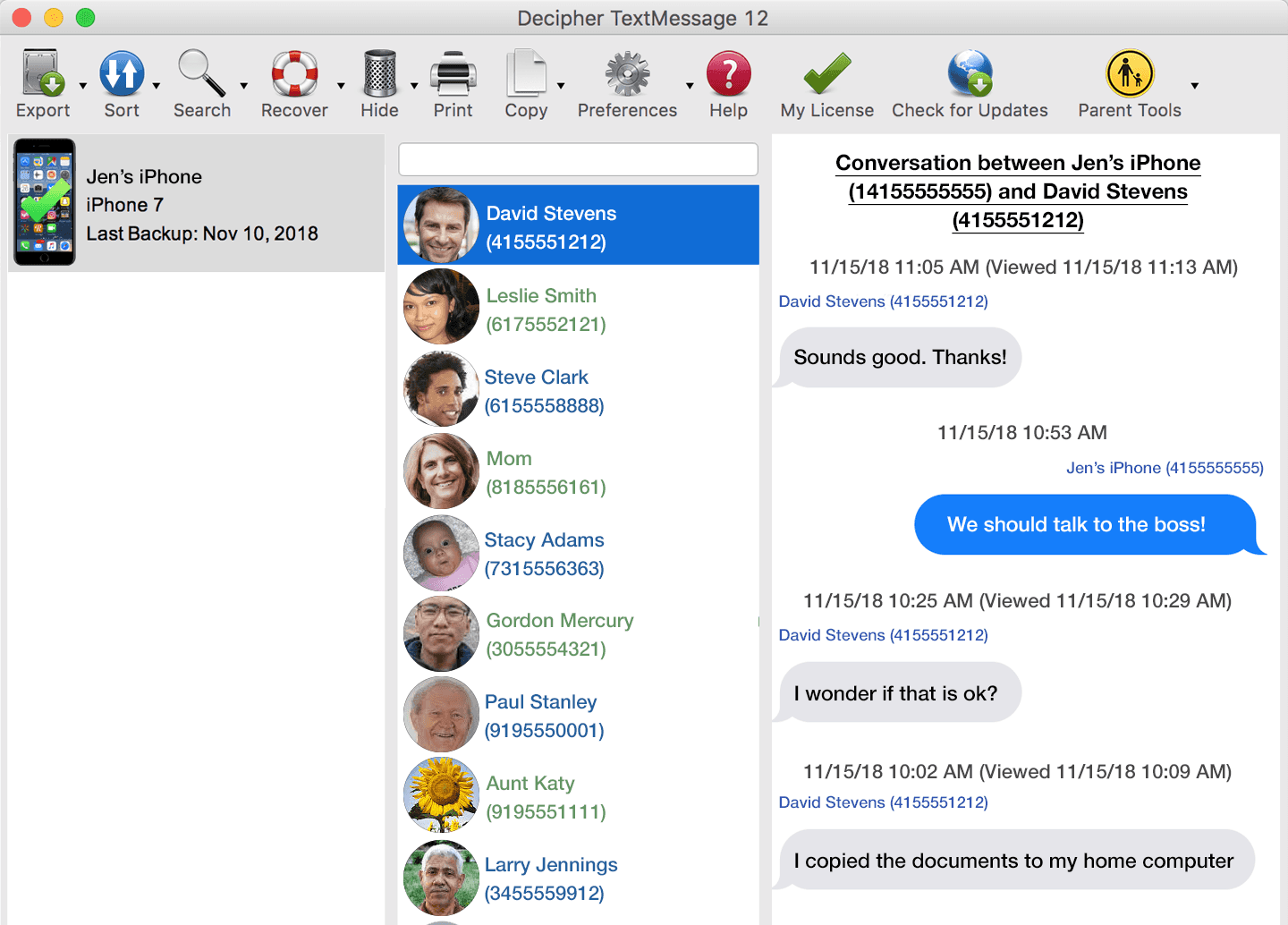
devices contain much information that could be interesting during a police investigation One of the most used smartphones, to date, is the Apple iPhone You can assume mobile phone forensic suites appear on the market, the problems of mobile You can specify in the settings in iTunes how often you will do backups |